AskTheAdmin is back again with another “how to” for the GAS readers. Today’s tutorial will be covering a technique that will allow you to reset your lost 2003 Active Directory Administrator Password.
Don’t worry, it happens to the best of us and you are not alone. I have never had this happen to me in a production environment but it did a few times in test domains.
This article assumes that you forgot the AD admin password, someone changed it on you, or you are recovering from an attack.
This is not meant as a how to hack your company’s Active Directory – nope, not in any way, shape, or form. In case you decide to use this tutorial for nefarious purposes, we can not be held liable for your stupidity. With that said let’s move on.
If you are trying to recover a local admin password from Windows XP, Vista, 2000, or NT, please refer to last week’s article on how to reset you local admin password.
If you are still reading this then you need to regain access to your Active Directory administrator account.
To do this you will need the following:
- Physical access to the domain controller that you are locked out of.
- Your local administrator’s password. (If you do not have this one as well, you can use the tool we wrote about last week to recover non-AD admin accounts).
- You will need Internet access to download two files from Microsoft’s resource kit unless you have them on CD. I found them online here: They are called SRVANY and INSTSRV.
- You will also need to be able to reboot the Domain Controller and have it offline while you do your magic. Note: This means users that log-on to this domain controller will not be able to authenticate while it is down.
- And of course you need to be comfortable with the command line and modifying your registry.
Aright then, let’s get cracking! (no pun intended!)
1. Restart Windows 2003.
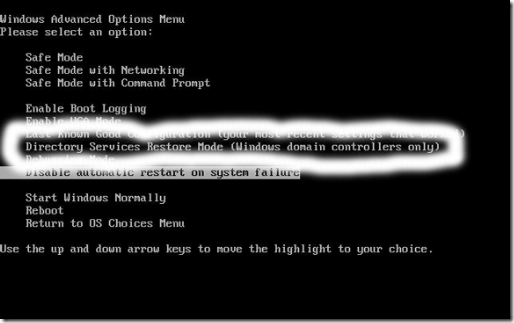
2. Boot into Directory Restore Service Mode.
Note: When the box restarts, you need to hit F8 (just like you do when you want to access safe-mode) and then choose Directory Restore Service Mode from the menu. This option disables your Active Directory but gives you full access to the box.
3. It will take a few moments for your login prompt to appear. When you see it, you will need to log on to this machine as the Local Administrator aka Directory Restoration Admin.
You are now in. You have full access to the system sans active directory. You can start and stop services, access files, change local accounts and shares, but we still cannot touch the AD domain password. Close but no cigar.
We need to install SRVANY, the link to download it is above. This Microsoft app turns any executable into an NT Service. Not just any service either, a service that runs in the system context. Any service created with SRVANY will have full system access. In case you don’t know, a service on a NT machine allows an application to be run automatically by the system without user intervention, like IIS or DHCP.
With that kind of system access, you can change the domain admin’s password without a problem. So now, how are we going to use this information to get a service in the system context that will change our active directory administrator’s password?
Keep reading!
Here is the trick: We are going to use the SRVANY application to make windows run a command prompt in the system context.
Do you see where I am going with this yet?
We have to copy SRVANY and INSTSRV to a folder containing CMD.exe. For this instance I created c:\recovery. Now in my c:\recovery directory I have three files. They are srvany, instsrv and cmd.exe.
Note: If you are having problems finding cmd.exe, it lives in your system32 directory.
Open a command prompt by going to start, run, type “cmd” in the field, and press ok. Navigate to the folder containing srvany, instsrv and cmd.exe. Then type:
instsrv.exe FixPass “c:\recovery\srvany.exe”
This creates a service called FixPass that runs via the srvany.exe application. Remember srvany can run any exe as a service.
Now we need need to setup srvany to do our bidding. For this step we need to modify the registry.
Start regedit, and open this key:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\FixPass.
Create a new sub-key under FixPass called Parameters and add two new values:
Name: Application
Type: REG_SZ (string)
Value: c:\recovery\cmd.exe
Name: AppParameters
Type: REG_SZ (string)
value: /k net user administrator new_domain_pw
The first entry tells FixPass to run cmd.exe. The second gives it its parameters aka our password changing command.
‘net user username password’ is how we use the command line utility to set a new password.
Replace new_domain_pw with the password you want your Active Directory Administrator to have.
Now let’s open our services console by going to:
Start –> Run and type:
services.msc
Hit enter. Now find and open the FixPass service property tab. You do this by right clicking on the service and choosing properties.
Change the service’s startup mode to Automatic.
This next step is very important. Click on the Log On tab of the FixPass services properties and enable the option to “Allow this service to interact with desktop”. Without this your password change will fail.
The plan is in place. Let’s review. We have SRVANY, INSSRV and cmd.exe in a folder. We set the registry to have srvany run a command prompt that will execute our change pw command. We set the service to run automatically and allow it to interact with the desktop. Now on startup the system will run the netuser command and reset the domain admin password.
The hard work is done. Let’s see if we succeeded. We need to reboot Windows into normal mode and wait for the login screen. After the prompt appears, wait 60 seconds. It can take a shorter time but let’s just wait to be sure.
You can use this time to reflect on how you let this happen and how it won’t ever happen again.
Ha!
Our command ran in the background and your password should now be changed. Log in using the new password we set way back in the procedure. If all went well you should be logging in as we speak.
Now you are the domain admin again – feels good right?
Now after your successful logon, when the desktop comes up you will have a command window open. This is the same command window that executed your script. We will now delete our service and undo our mods so that it doesn’t change your password on every reboot.
Ah… Forgot about that didn’t ya?
Type these commands in this order:
net stop FixPass
sc delete FixPass
The first one stops the FixPass service and the second one removes it.
Remove the folder you stored your files in (I used c:\recovery) and that’s it. Change your password to something you will remember. No really something you will remember in the future so you don’t have to go through this again!
About the author: Karl Gechlik is a Microsoft certified administrator that spends his time solving complex technology issues during the day and at night enjoys his beautiful wife and wonderful 16 month old daughter. Karl writes for many online sites including http://www.askTheAdmin.com , come stop by and tell him GAS sent you!